Writing an app for the Atlassian cloud platform? Were you aware you need to meet security requirements for your app? Does this all seem oddly specific for a random blog post? Is it truly a cliche to start a post with a collection of questions? – Probably. I’ll stop now.
In today’s post, I’m going to describe how you can meet (most) of the Atlassian Security Requirements by simply fronting your Atlassian connect app with Cloudflare.
Getting Started
Ensure you have a Cloudflare account setup. If not, ensure you sign-up for a new account: https://dash.cloudflare.com/sign-up
Next, make sure you have your primary domain’s nameservers configured for Cloudflare. Cloudflare has a handy developer guide for this particular situation . If you require a more advanced setup, there are also docs for that too .
Ensuring your app’s subdomain is being proxied
From your site’s Cloudflare Menu, select DNS from the left-hand menu.
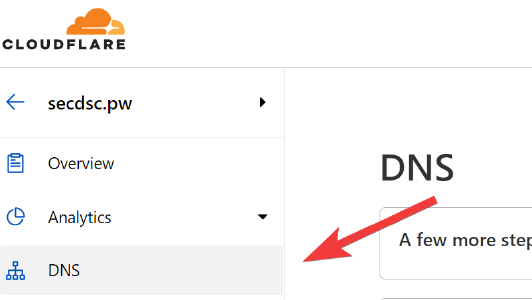
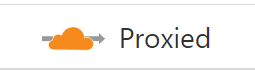
Find your app’s relevant DNS entry, and ensure it is Proxied.
Updating Cloudflare SSL/TLS Settings
Now that all the necessary preparations have been checked, we can update a few Cloudflare settings to make your app compliant with the Atlassian SSL/TLS requirements.
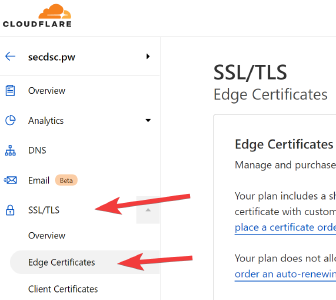
First off, let’s navigate to the SSL/TLS menu, then click Edge Certificates from the left-hand menu.
Enabling HTTP Strict Transport Security (HSTS)
We enable HSTS to meet Requirement #1 of the Atlassian Security Requirements for Cloud Apps .
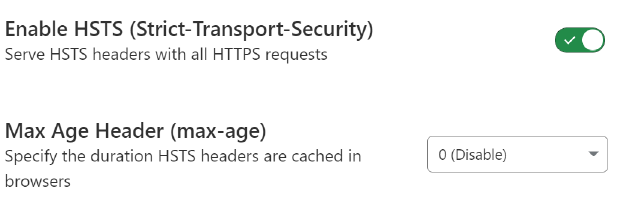
Under the SSL/TLS -> Edge Certificates Cloudflare menu, find the HTTP Strict Transport Security (HSTS) section by scrolling down.
Click Enable HSTS, carefully read the acknowledgement and then proceed.
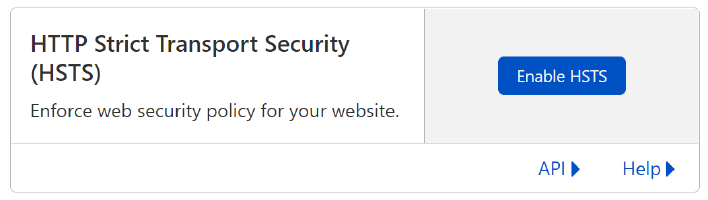
On the Configure screen, ensure you enable HSTS and for safety set the Max Age to 0 for now. This will ensure you can confirm things are working before setting the HSTS Max Age to be a longer value.
Setting Minimum TLS Version
We restrict the TLS version accepted by our app to meet Requirement #1 of the Atlassian Security Requirements for Cloud Apps .
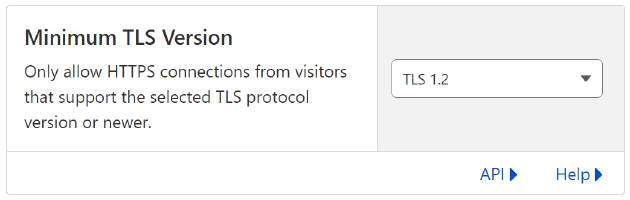
Under the SSL/TLS -> Edge Certificates Cloudflare menu, find the Minimum TLS Version section by scrolling down.
Set the minimum TLS version to TLS 1.2.
Let’s test our changes
Let’s confirm that everything looks good from an external scanner’s perspective.
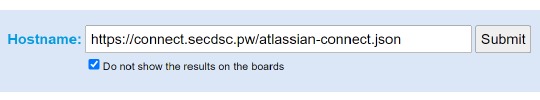
We can use Qualys’ SSL Labs tester to see what our app now shows to an external visitor. Navigate over to: https://www.ssllabs.com/ssltest/ and enter your app’s connect descriptor URL.
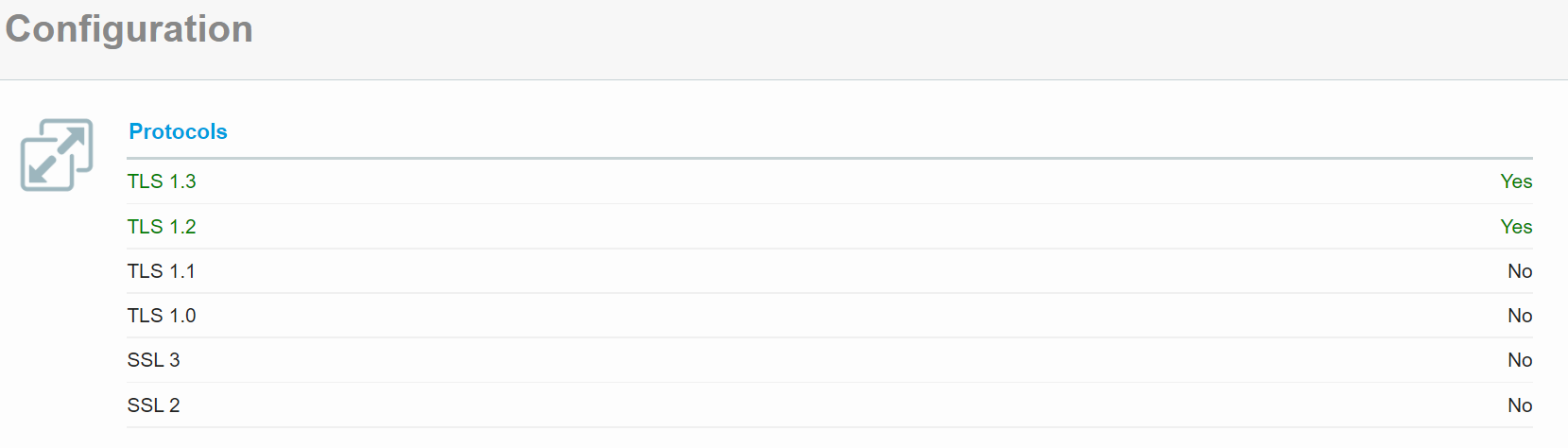
Once one of the IP addresses finishes being scanned, confirm that only TLS 1.2 and higher protocols are accepted. All lower protocols (eg. TLS 1.1, TLS 1.0, SSL 3) should not be accepted.
Now, you will need to go and update your HSTS settings to be something with a longer Max Age than 0. You can choose 1 Month if you are concerned about breaking access to your site. You can increase this value over time as your confidence grows.
And you’re done!
Wait, what? That was only two minor tweaks. You are correct, but those are two things that are notoriously difficult to setup from application code / server configuration. These are also the primary things Atlassian is automatically scanning for to confirm your app is compliant .
Cloudflare will also ensure your HTTPS certificates never expire, since they manage them. They will also ensure you do not lose control of your domain by sending you email reminders about domain renewal.
Comments